Scenario
You are trying to register an application at SharePoint site with appregnew.aspx page and you are getting an error or notification message “Your SharePoint tenant admin doesn’t allow site collection admins to create an Azure Access Control (ACS) principal“.
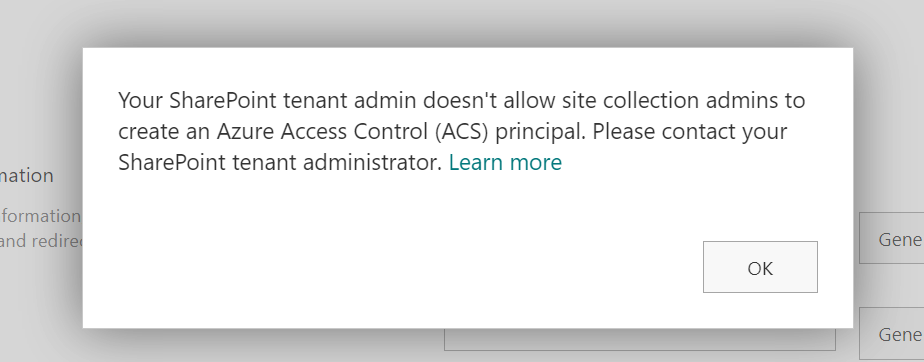
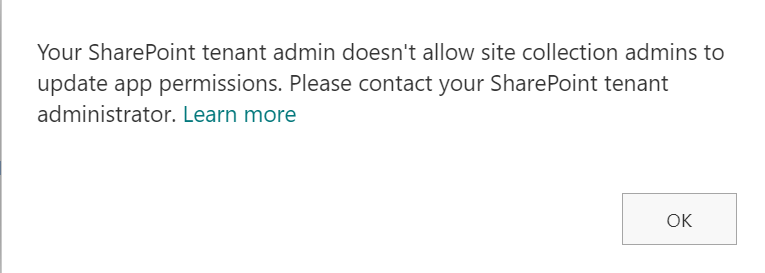
Or you are trying to provide ACS-based permissions for an application to SharePoint site with appinv.aspx page and you are getting “Your SharePoint tenant admin doesn’t allow site collection admins to update app permissions. Please contact your SharePoint administrator.”
You can still view and even delete your apps permissions from /_layouts/15/appprincipals.aspx page:
Reason
This is due to a recent update to Microsoft 365 (tenant governance security measures enhancement MC660075) implemented by Microsoft in Aug/Sep 2023. According to the update, only tenant administrators can create or update ACS service principal by default.
The root cause for this is that the Microsoft is pushing developers out of that legacy ACS-based SharePoint Apps-only service principals towards Azure-registered applications with Sites.Selected API permissions as they are more secure etc.
In Nov 2023 Microsoft announcement retirement of ACS principals.
Key differences between ASC and Sites.Selected are:
| ACS-based SharePoint app/permissions | Apps registered in Azure with Sites.Selected API permissions |
|---|---|
| Support authentication with client secret only, Secrets are valid for 1 year exactly. | Support authentication with client secret and/or certificate, custom expiration time. |
| Support granular access to SharePoint site, e.g. to site collection or web (subsite) or a specific list or library. | Support only access to entire site collection (but Microsoft says granular access is coming) |
| Support only classic SharePoint REST API and CSOM | Support both – classic SharePoint REST API and CSOM and Microsoft Graph API |
| App id (client id) is created via appregnew.aspx at a specific SharePoint site by site collection administrator (disabled in Sep 2023). | App id (client id) is created in Azure portal (Entra Id), API Sites.Selected permissions are configured via Azure portal (Entra Id) and require tenant admin consent. |
| Permissions for the app to a site are provided at the site by site collection administrator via appinv.aspx page (disabled in Sep 2023). | Permissions for the App to to a specific SharePoint site are provided via Graph API by SharePoint admin with PowerShell script. |
Solution #1 – switch to Sites.Selected
- Register an application in Azure (via Entra Id – Azure portal GUI, PowerShell script or your company’s specific helpdesk/servicedesk request)
- Update the app so both – MS Graph API Sites.Selected and SharePoint Sites.Selected permissions are configured, then
- API permissions must be consented – so you’d seek/request your tenant admin consent
- Obtain and upload client certificate (recommended) or generate client secret
(at this moment you should be able to authenticate to tenant) - Request access for the app to a specific SharePoint site – your SharePoint service admin should be able to do that
(at this moment you should be able to authorize to your SharePoint site). - Validate your app has access to the target SharePoint site with PowerShell
(check validation scripts below under References). - Use recommended by Microsoft technique, code samples are available for the most popular languages/platforms – Python, C#, Java etc. (check below under References).
- Secure your certificate and/or secret. It is not a good idea to use hard-coded secrets, so consider using special services/storages for secrets (aka Vaults)
If you are hosting your application in Azure – consider using managed identity.
Step-by-step guide with screenshot – how to get app with Sites.Selected permissions
Video guide on using Sites.Selected to access SharePoint as application:
There are 3-rd party (and Microsoft) apps developed using classic approach (examples – Azure data Factory, Alteryx). So in some cases Sites.Selected permissions are not enough to get access to SharePoint.
Solution #2 – admin to register/update an ACS app
This option is acceptable if you have existing application that require ACS-based access.
This option is not recommended for new development, as ACS is deprecated and scheduled for retirement.
Microsoft (MC660075 in Message Center): “site collection admin will be unable to register app or update app permissions through above pages unless authorized explicitly by the SharePoint tenant admin” and “With this update site owners will not be able to register/update apps unless the tenant admin explicitly allows it.”
That is incorrect. Site collection admin cannot register app (appregnew) or provide permissions to the app (appinv) anymore. Tenant admin does not authorize site collection admins. Instead tenant (or SharePoint) admin can register an app or provide permissions to the app at a specific site (not changing the entire default behavior back…). But there was no such option (!) in the middle of October 2023, when this feature was enabled at all tenants. Even having a SharePoint admin or tenant admin permissions – if you tried to register an app with AppRegNew.aspx – you got the same error message “Your SharePoint tenant admin doesn’t allow site collection admins to…”.
Later (Checked today – Nov 6, 2023) it seems like Microsoft has implemented it! E.g. now SharePoint or tenant admin is able to register an app with AppRegNew.aspx or update it with AppInv.aspx at any specific site collection. SharePoint or tenant admin must also be among this site collection admins.
It is ok (and I’d say the preferred way) to provide ACS permissions to the app registered in Azure, so do not register apps in SharePoint anymore (do not use AppRegNew.aspx).
Bottom line: if ACS-based permissions are required for app here you go:
- register application in Azure (Entra id)
- activate your SharePoint service/tenant admin role
- ensure you are also target site collection administrator
- navigate to the site appinv.aspx page – e.g.
“https://yourtenant.sharepoint.com/sites/yoursite/_layouts/15/appinv.aspx”
and us Azure registered app (client) Id. E.g. for lookup provide- Azure registered app (client) Id for – click lookup
- localhost as app domain
- https://localhost as redirect url
- Permission Request XML – depending on permissions you need, e.g. for full app access to entire site collection:
<AppPermissionRequests AllowAppOnlyPolicy="true">
<AppPermissionRequest Scope="http://sharepoint/content/sitecollection"
Right="FullControl" />
</AppPermissionRequests>Solution #3 – step back (not recommended)
It is possible to switch back this new default behavior that prevents site collection admin to register/update apps at SharePoint. This is done with PowerShell command
Set-SPOTenant -SiteOwnerManageLegacyServicePrincipalEnabled $trueTo run this command – you’d need to be a SharePoint service or tenant admin.
But this will be a step back on your journey in improving m365 tenant safety, as after that you’ll have a self-registered service principals out of control again. So devs will be using it not being aware of ACS retirement and when Microsoft switch off ACS – it will be a disaster, as all app will stop working. That is why Microsoft implemented this feature to soft-disable ACS and allowed us 2 years to redesign or apps and migrate from ACS to Entra Id apps with Sites.Selected. So this solution is not recommended.
In case you really need an exception to provide an ACS-based service principal – there is Solution number 2.
Full text of Microsoft’s MC660075 message
(Updated) SharePoint admin control for App registration / update
Tag
MAJOR UPDATE ADMIN IMPACT FEATURE UPDATE
Message Summary
Updated August 30, 2023: We have updated the content below for clarity. Thank you for your patience.
This is an enhancement to the security measures for administrative governance that modifies the default procedures for SharePoint app registration via AppRegNew.aspx page and permission updates via AppInv.aspx page. Following the implementation of this change, site collection admin will be unable to register app or update app permissions through above pages unless authorized explicitly by the SharePoint tenant admin.
Upon attempting to register an application on AppRegnew.aspx page, a notification will be displayed stating “Your SharePoint tenant admin doesn’t allow site collection admins to create an Azure Access Control (ACS) principal. Please contact your SharePoint tenant administrator.”
Similarly, upon attempting to update app permissions on AppInv.aspx page, a notification will be displayed stating “Your SharePoint tenant admin doesn’t allow site collection admins to update app permissions. Please contact your SharePoint tenant administrator.”
Kindly note that app registration and permission update via Microsoft Azure portal are not impacted by this change.
When this will happen:
The rollout process is scheduled to commence in late August and is expected to conclude in mid-September.
How this will affect your organization:
With this update site owners will not be able to register/update apps unless the tenant admin explicitly allows it.
To modify the default behavior, the tenant administrator must execute the following shell command to explicitly establish the flag as TRUE, thereby superseding the default value of FALSE. The service principal can only be created or updated by the tenant administrator by default. However, when the flag is set to TRUE, both the SharePoint tenant admin and site collection admin will be able to create or update the service principal through SharePoint.
The shell command is: Set-SPOTenant -SiteOwnerManageLegacyServicePrincipalEnabled $true
Note: The property ‘SiteOwnerManageLegacyServicePrincipalEnabled’ becomes visible in tenant settings after SharePoint Online Management shell is updated to 16.0.23710.12000 or a later version. But before this rollout, the value will always be TRUE even explicitly set to FALSE. It will only automatically be switched to FALSE as the default value after the rollout is launched.
What you need to do to prepare:
No proactive measures are required to prepare for this change. Nevertheless, it is advisable to inform your users of this modification and update any relevant documentation as necessary.
Pingback: Sites.Selected API permissions for SharePoint access ⋆ Vladilen Microsoft 365 engineer
Pingback: Automating Sites.Selected permissions provisioning ⋆ Vladilen Microsoft 365 engineer
Pingback: Microsoft Azure Data Factory connect to SharePoint ⋆ Vladilen Microsoft 365 engineer
Pingback: Providing ACS permissions for app to access SharePoint ⋆ Microsoft 365 engineering
Thank you for detailed article.
About solution #2, Even if this is done, it will stop working after 2026, is that right? (Since its still based on ACS)
Yes, with the recent announcement from Microsoft regarding ACS and Add-Ons retiring this #2 is considered as temporary solution. Thanks for the reminder, I’ll update accordingly.
Thanks for a great article! We need to connect Azure Data Factory via AAD AppReg/service principal to a single SPO site collection, and solution #1 (Sites.Selected) seems the way to go. We need to swing it, as there seems to be no official documentation how to do it. But your step-by-step list helps a lot. Thanks!
AFAIK Azure Data Factory requires ACS token, so you’d provide (request your admins to) ACS access for your app.
Hopefully Microsoft will update ADF before 2026.