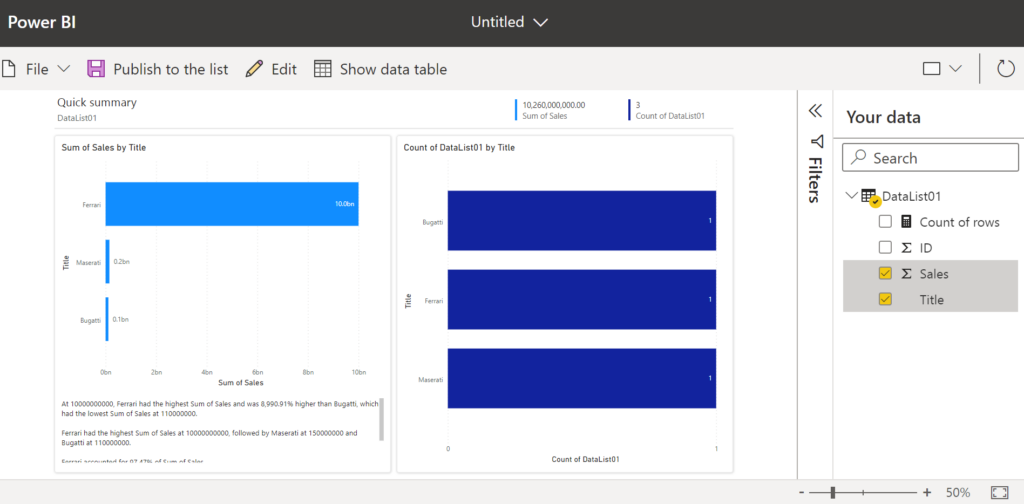
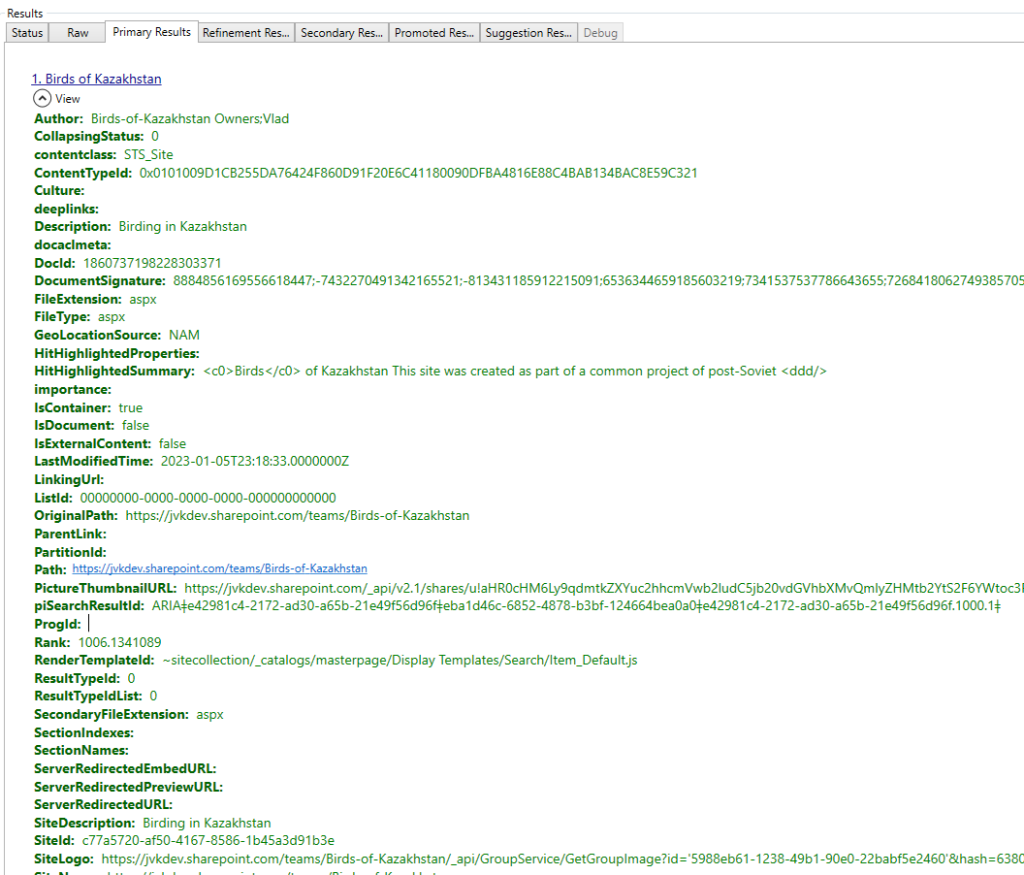
Microsoft announced SharePoint Archive in 2023 and make the feature generally available in Apr 2024. Though there are good Microsoft’s articles on how to enable and configure SharePoint Archive, as well as some FAQ pages, there are still a lot of questions regarding behavior details, e.g.
- what happens with Team content if the group-based site is Archived
- is there an API or how do we archive/restore sites programmatically
- would MS Graph Search API work for archived sites
I have just activated the feature and I’m planning updating this page with my gotchas and findings…
Reactivation fee
How much is to restore a site from Archive?
In the example below Microsoft charges me $1 to restore a simple OotB site with no documents:
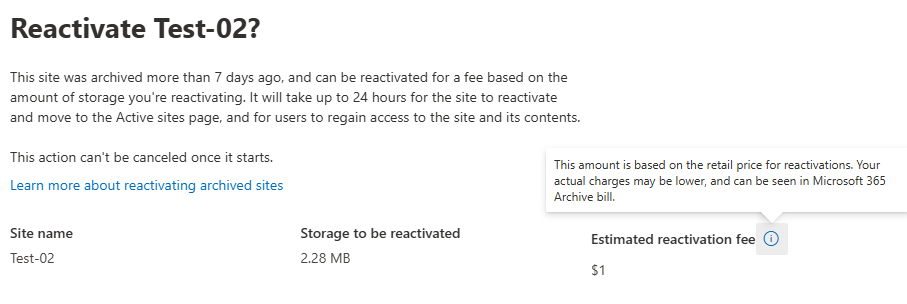
Microsoft says “This amount is based on the retail price for reactivations. Your actual charges may be lower, and can be seen in Microsoft 365 Archive bill.”
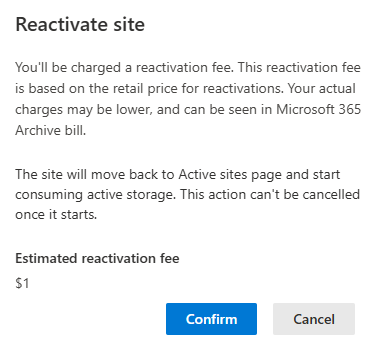
Another confirmation is requested:
Reactivate site.
You’ll be charged a reactivation fee. This reactivation fee is based on the retail price for reactivations. Your actual charges may be lower, and can be seen in Microsoft 365 Archive bill.
The site will move back to Active sites page and start consuming active storage. This action can’t be cancelled once it starts.
Estimated reactivation fee
$1
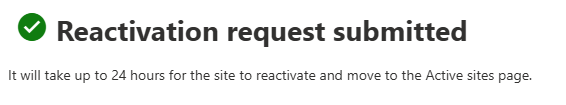
After a few days I saw cost “<0.01$”
===========
To be continued…