Before we can make a call to Microsoft 365 from our code – we need to be authenticated. There are many kinds of authentication flows that Microsoft supports. For more details – please refer to Microsoft Identity Platform documentation but in short – there are two major kind of authentications – as a current user and as a daemon application and in both cases we need an application to be registered in Azure.
Briefly here is what you need to have for your custom application to authenticate to Microsoft 365:
- register Application in Microsoft Azure
- configure Authentication blade (for interactive apps)
- configure Secrets or Certificates (for daemon apps)
Register Application in Microsoft Azure
1. You’d go to https://portal.azure.com/
2. Type app registration in search and select App registration

Update (July 2025) – the search for “App reg” is not working… But you can go to App registrations from Entra Id:
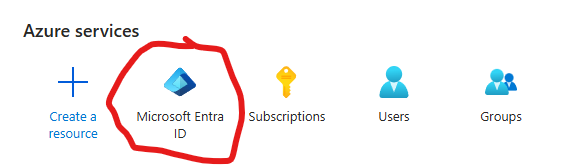
3. Select “New registration”

4. For now, you’d just need to provide your application display name and leave other fields as default – Single tenant and no redirection Url, then click “Register”

5. If you are seeing an error message telling that your are not allowed to register an app – you’d reach your AAD/EntraId/Global admins so they can register an app for you.
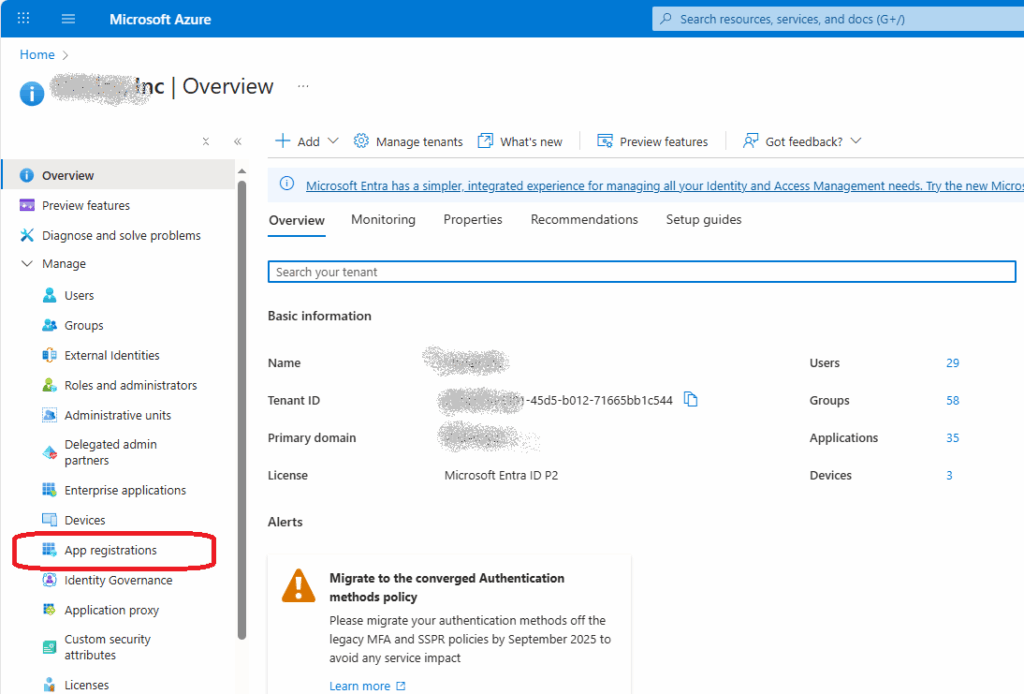
6. Under Azure Portal App Registrations you should be able to see your app:

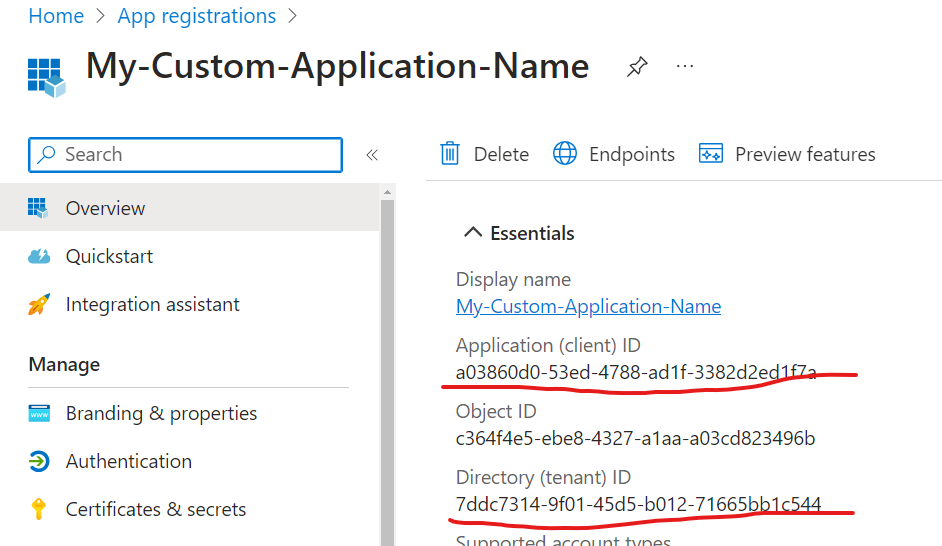
7. Under Overview blade notice you Client Id and tenant Id:
Configure Authentication blade for interactive apps
Azure apps for interactive authentication are configured differently (check MS app types and authentication flows) for different scenarios/platforms.
Here is a good article from MS. Microsoft Graph quick start can register an app for you. Microsoft publish tutorials for .net, Go, Java, JavaScript, PHP, Python, TypeScript…
In a few words, you’d need to add Platform as below
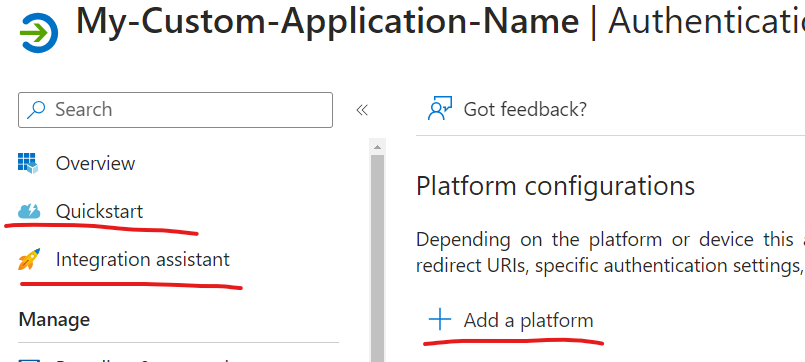
manually if you know how to configure it.
Otherwise, Quickstart and/or Integration assistant might help you.
Here is how I configure apps for interactive user authentication for PowerShell.

You do not need Certificates or Secrets for authentication as current user.
Configure Secrets or Certificates for daemon apps
Daemon apps (aka service apps, also called background jobs) – all kind unattended access scenarios do not require configuration under Authentication blade – but require Secrets or Certificate. You’d need to be familiar with certificates, as certificates considered as more secure way to authenticate and some authentication flows allow secrets, but some require certificates.
So for daemon apps you need a secret and/or certificate:
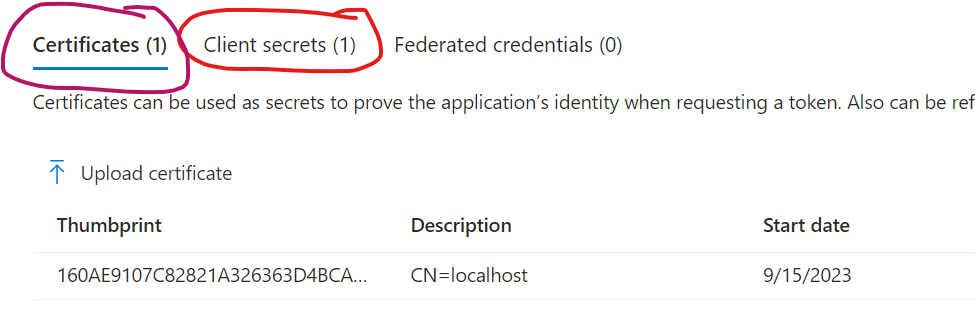
Here is how I configure daemon app for PowerShell.
Having an app configured as above – you should be able to authenticate against Microsoft 365 Graph API, but should not have access to resources, as app is not authorized yet.
Pingback: Search through Microsoft 365 SharePoint from code
Pingback: Search Microsoft 365 content programmatically ⋆ Microsoft 365 engineering
Pingback: Using SharePoint REST API from Python code ⋆ Microsoft 365 engineering
Pingback: Get list of new m365 SharePoint sites or teams with PowerShell ⋆ Vladilen