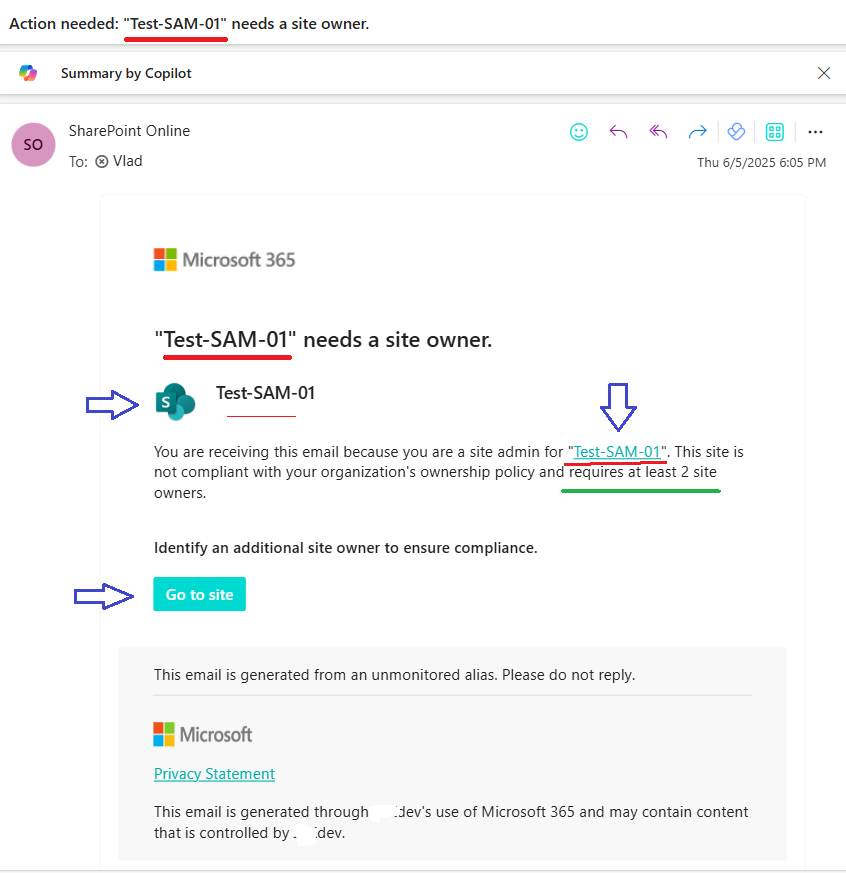
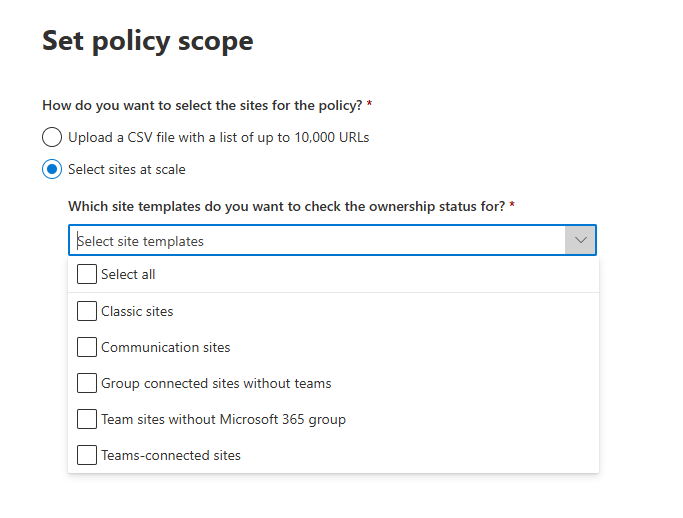
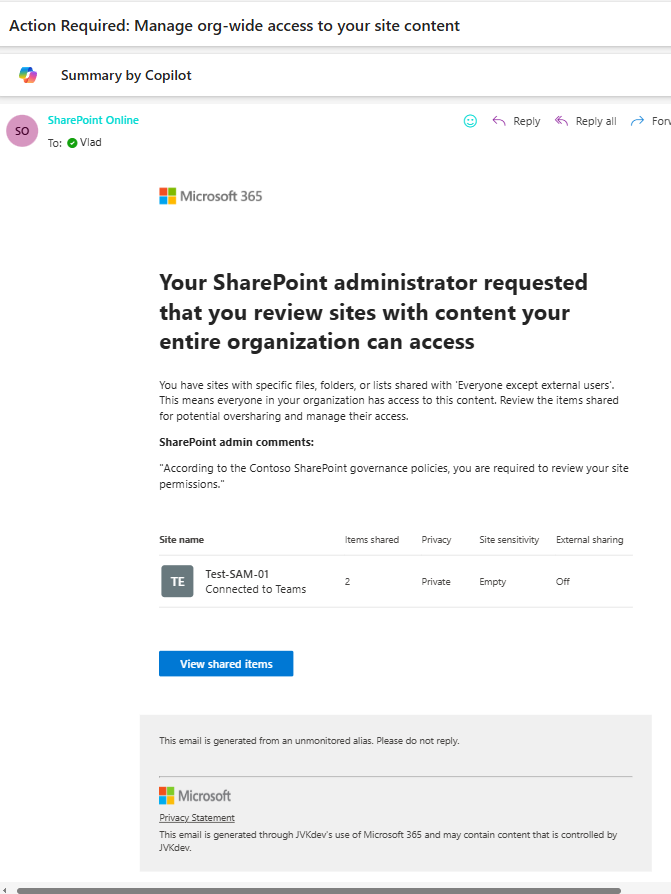
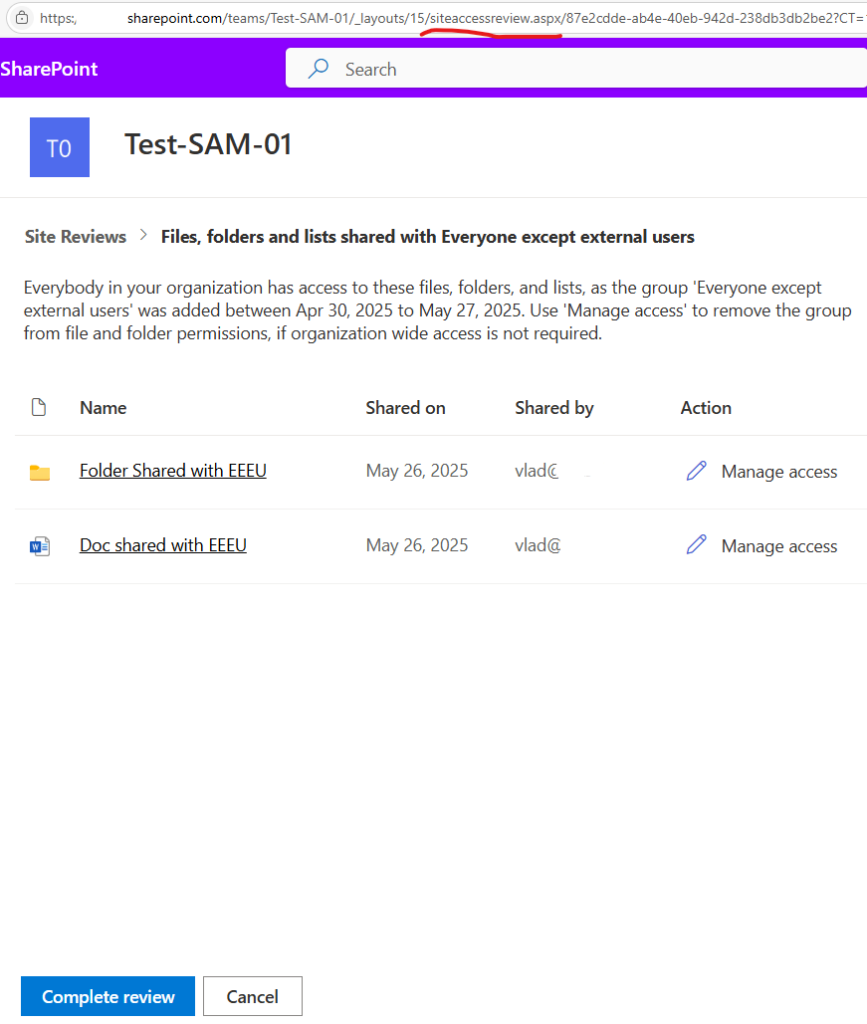
Oversharing remains one of the most persistent challenges in SharePoint Online. With the introduction of Microsoft Copilot and its AI-powered search capabilities, the issue has become even more visible—and more urgent to address. Microsoft has acknowledged this by introducing the SharePoint Advanced Management suite, aimed at helping administrators to bolster content governance throughout the Microsoft Copilot deployment journey.
Why Does Oversharing Happen?
In most cases, oversharing is unintentional. Based on my experience, the root causes typically fall into four categories:
- Unaware Sharing: A user shares a site, library, or folder without realizing it contains sensitive information.
- Unaware Uploading: A user uploads sensitive content to a location that is already broadly shared.
- Human Error: Mistakes like selecting the wrong group or sharing a folder instead of a file.
- Convenience: Users opting to share with “Everyone” to avoid the hassle of managing individual permissions.
Why It’s a Bigger Problem Today
In the past, search in Microsoft 365 was content-driven—you had to know what you were looking for. Today, search is context-driven. Microsoft 365 proactively surfaces content with suggestions like “Here’s what might be interesting to you” or “Here’s what others are working on.” This increases the risk of oversharing content being exposed.
Separate issue, non-technical, but related to the subject – not every user knows that search in Microsoft 365 is security-trimmed, i.e. provides results from only what this specific user has access to. Sometimes people might think of Microsoft 365 search the same way as general internet search (If a can see it – then everyone can see it, or why my private documents appear under Bing search?).
The Admin Dilemma
As SharePoint administrators, we’re caught in a classic catch-22:
- Complex Microsoft products
- Users prone to mistakes
- Management demanding simple, fast solutions
What seemed like straightforward fixes for oversharing actually concealed the true issue, generating new problems, increasing admin burden, perplexing users, and ultimately hurting company productivity. Examples are (I would never do that):
- Exclude sites from search indexing (Set “Allow this site to appear in search results?” to No)
- Turn off Item insights, turn off People insights (turn off Delve)
- Truncate enterprise search with “official” sites only (via query)
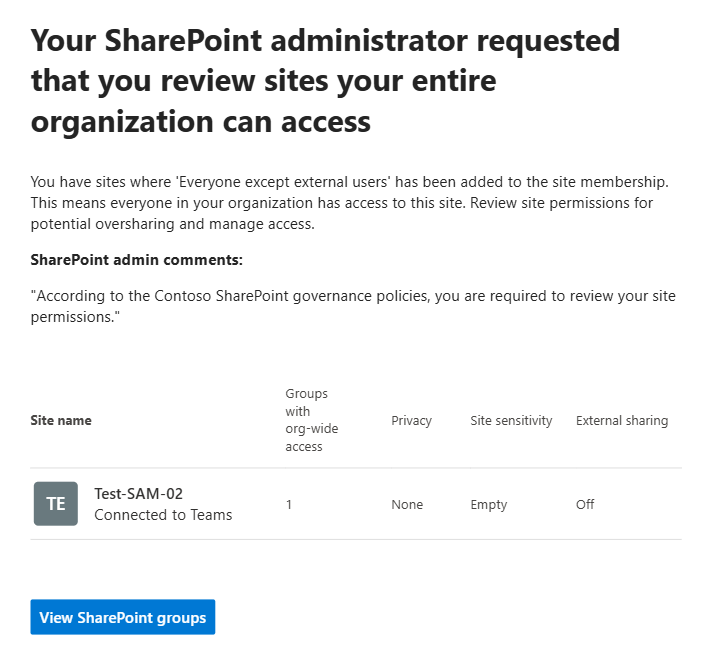
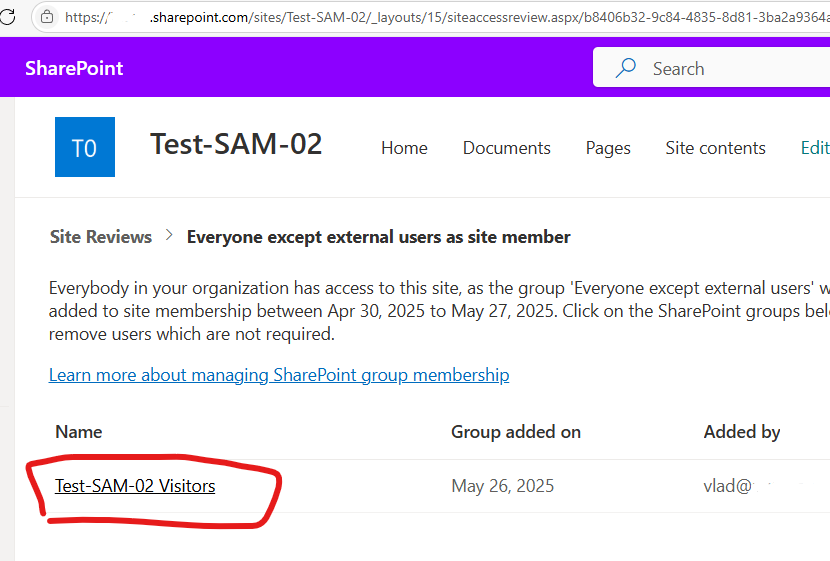
Microsoft offers two solutions: “Restrict discovery of SharePoint sites and content” and “Restricted SharePoint search”. Both solutions aimed to exclude content from search and from Copilot. Microsoft: “Restricted SharePoint Search allows you to restrict both organization-wide search and Copilot experiences to a curated set of SharePoint sites of your choice… and content users own or that they have previously accessed in Copilot.”. “With Restricted Content Discovery, organizations can limit the ability of end users to search for files from specific SharePoint sites.”
Microsoft clearly says that “limit the ability of end users to search” is a temporary measure that “gives you time to review and audit site permissions”… “to help you maintain momentum with your Copilot deployment while you’re implementing comprehensive data security”. Also: “Sites identified with the highest risk of oversharing can use Restricted Content Discovery to protect content while taking time to ensure that permissions are accurate and well-managed”.
Microsoft highlights that “Overuse of Restricted Content Discovery can negatively affect performance across search, SharePoint, and Copilot. Removing sites or files from tenant-wide discovery means that there’s less content for search and Copilot to ground on, leading to inaccurate or incomplete results”.
And finally “Restricted Content Discovery doesn’t affect existing permissions on sites. Users with access can still open files on sites with Restricted Content Discovery toggled on.”. I.e. solutions “Restricted SharePoint Search” and “Restricted Content Discovery” do not solve the root cause of the problem (oversharing), but make the problem less visible.
With over 15 years of experience in SharePoint and more than a decade working with Microsoft 365 and Azure—including large-scale tenants—I’ve seen this problem evolve. Now, with Copilot in the mix, it’s more critical than ever to implement a robust access management strategy.

How to solve the real oversharing problem
(My Ideal “No-Oversharing” Tenant Configuration)
Here’s what I would recommend for minimizing oversharing in a Microsoft 365 environment (think of it as SharePoint Governance):
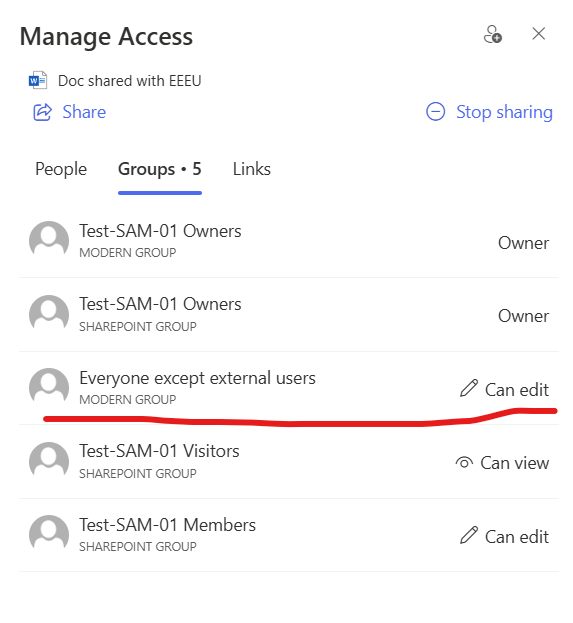
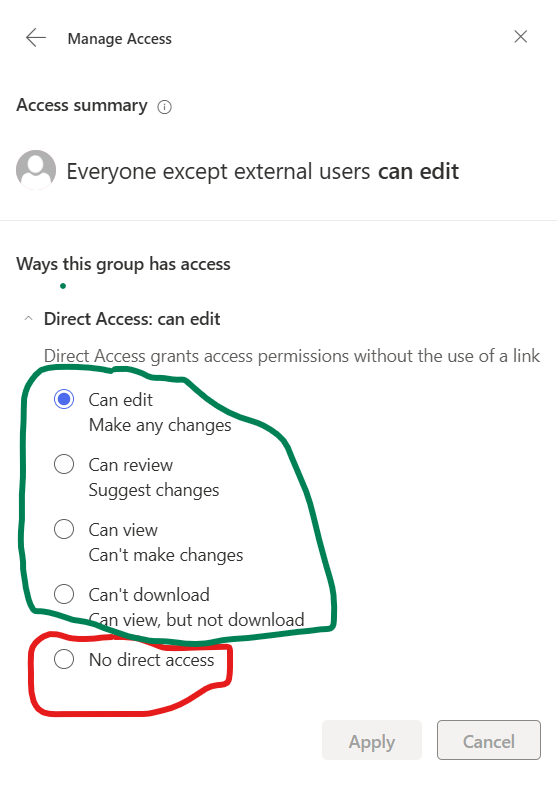
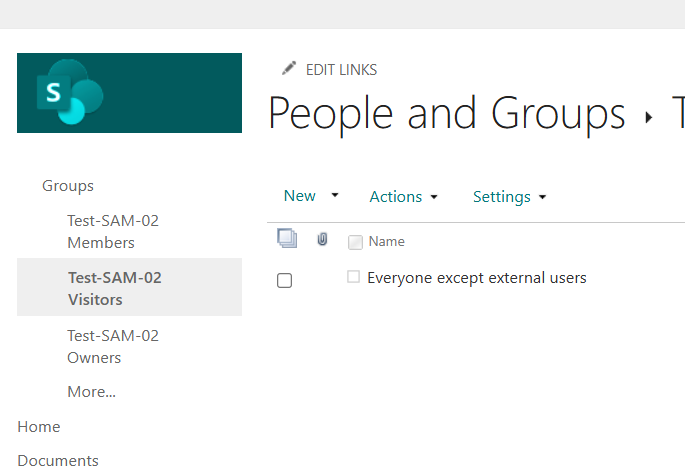
1. Remove “Everyone” and “Everyone Except External Users”
Disable these groups in the people picker to prevent broad, indiscriminate sharing. Instead, provide other options for sharing content with larger audiences (see below).
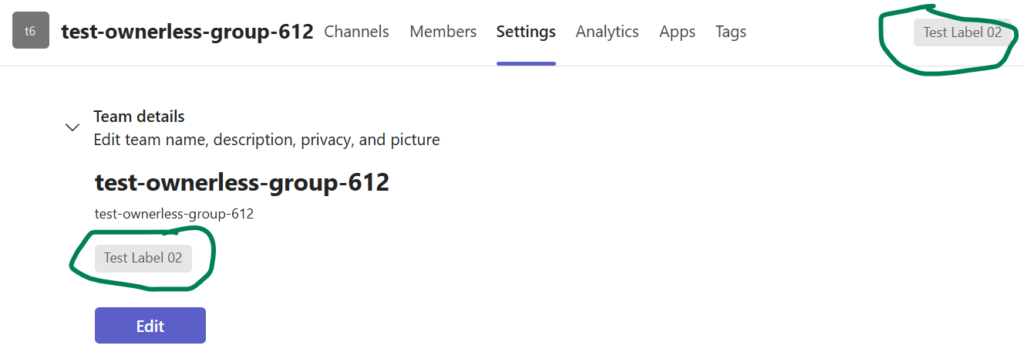
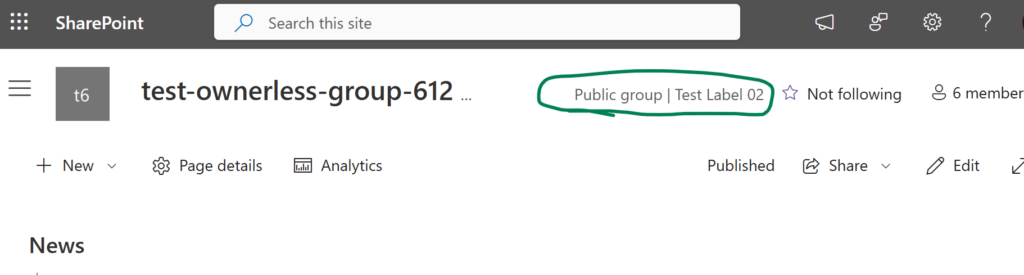
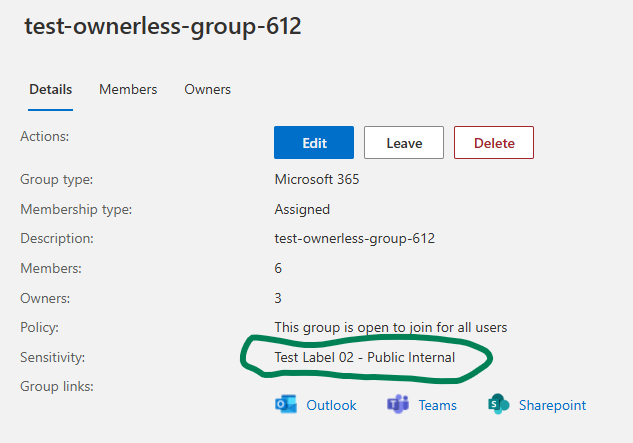
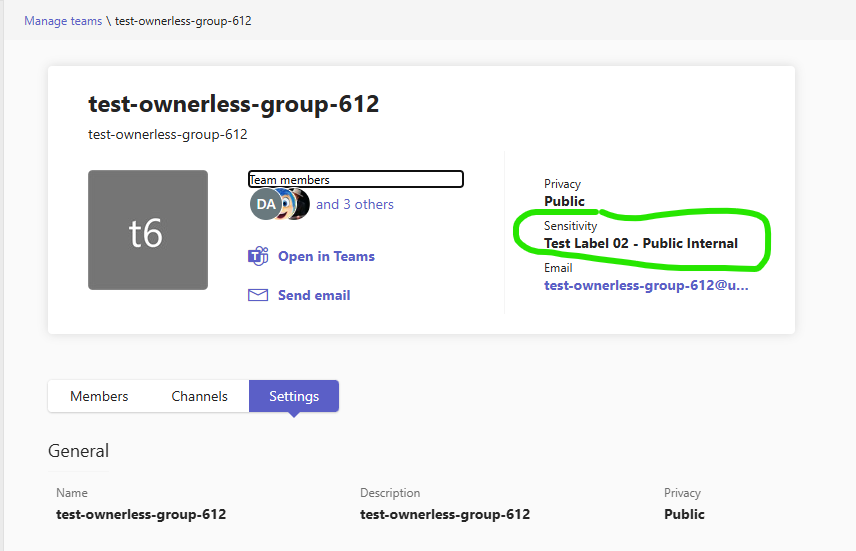
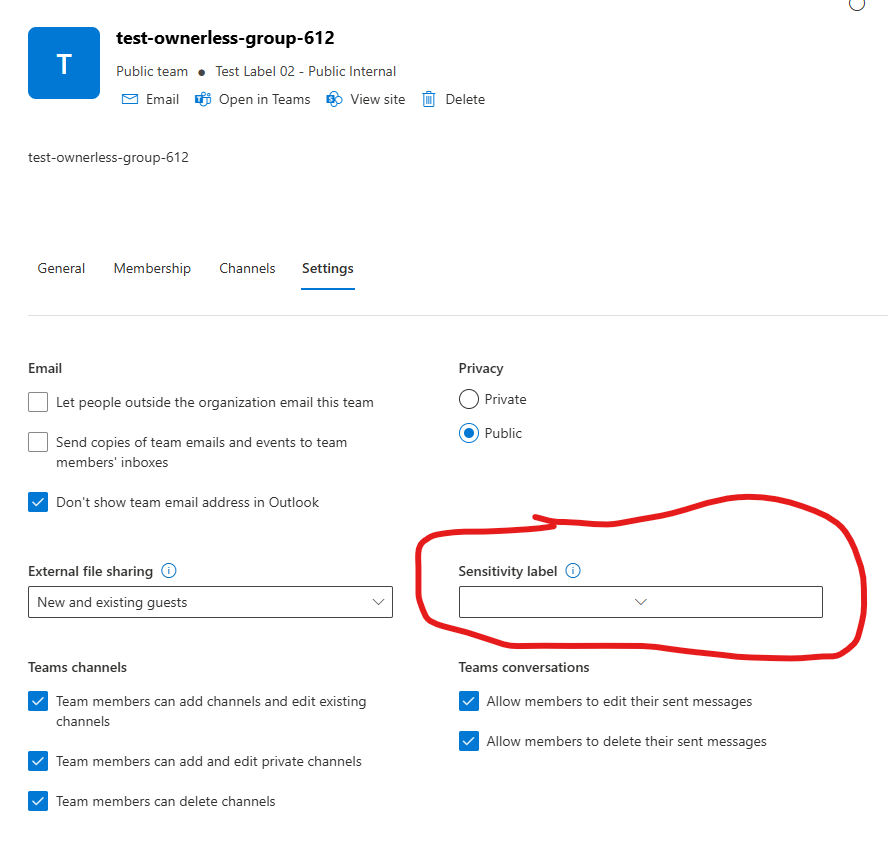
2. Implement Sensitivity Labels for Sites
- Enforce mandatory sensitivity labels for all sites.
- Labels should control site visibility (e.g., Private, Public) and be clearly named
The label is visible across all interfaces—Teams, SharePoint, libraries, lists, folders—so users always know how wide the content is shared from the sensitivity label.
3. Empower Users with Guardrails
- Allow users to create Teams and communities, but enforce sensitivity labels.
- Enable requests for standalone sites (Team or Communication) with required labels.
- Disallow private or shared channels under public Teams to avoid label mismatches (e.g., a private channel labeled “Public”).
Benefits of This Approach
Once implemented:
- Users will always know whether a site is private or public.
- Sharing with “Everyone” on private sites will be technically impossible.
- Users needing broad access can request public sites, e.g.
- Public Teams for collaboration with everyone (allows read/write access)
- Communication site for publishing information (allows read only access)
Yes, this may lead to more sites and Teams. Yes, this may lead to more tickets from users who at private site wanted to break permissions as usual and share list or library or folder with everyone. Yes, we would need to develop automation that can help manage the scale. But that’s a worthwhile trade-off for reducing oversharing!
More to consider
Large Custom Security Groups
There might be Large Custom Security Groups in tenant. What if the user wants to share site with one of these Large Custom Security Groups? What kind of site that would be? Private? Public?
Consider the following. When a team owner adds a security group to team members – it’s not a group added, but individual users. That makes sense – all team members can clearly see who are the other team members. That makes the team private. Private team should not be additionally shared at SharePoint site level. Only permissions should be provided through team.
Public team – as well as public standalone site – can be shared with EEEU. But what if the requirements are not to share the site with “Everyone…” but share with some other Large Custom Security Group – e.g. “All employee” or “All Central Office Users”? Can we do it? Should site be private or public in this case?
My opinion: site should be labelled as public. Site owner can request a public standalone site or create a team self-service, then site owner can remove “Everyone…” group from permissions and add a custom security group at any level.
Some orgs choose to recommend providing access to the standalone SharePoint sites via security groups vs SharePoint groups. So it is possible we have a private standalone site with access provided to security group (or m365 group). This is where an or should have their own policy – how big the group should be to be considered as large group and trigger site label as public. There are also dynamic security groups.
Automation Requirements
To support this model, we’ll need (at least) the following custom-designed solutions:
- Automated Site Provisioning: A request-and-approval process for creating labeled standalone sites.
- Channel Monitoring: A custom solution to detect and flag private/shared channels under public Teams, since there’s no out-of-the-box enforcement.
- Large Custom Security Groups Monitoring: make a list of large custom security groups users can share information with – and check on scheduled bases – if the site is shared with large custom security group – site must be labelled as public.
- Sharing site with “Everyone except external users” : If user accidentally removes “Everyone except external users” from public site – there must be an option for user to add “Everyone except external users” with permissions Read or Edit. Site can be shared with “Everyone except external users” only at the root site level and only if site labelled as Public.
Environment Clean-Up
To prevent oversharing, we should not only “from now on” follow the strategy described above, but also make sure our existing sites are compliant with our governance. This would be another challenge.