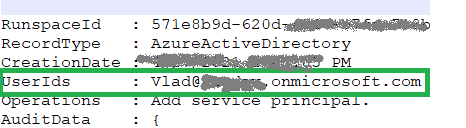
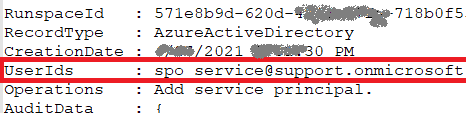
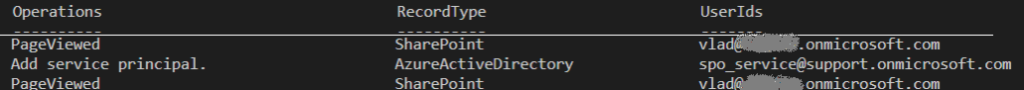
Yammer (now Viva Engage) is an internal (corporate) social network, and part of the Microsoft 365 suit of services. How do we work with Viva Engage programmatically? Can we read messages or search through communities? Can we get groups (communities) details and membership – etc. Is there an API we can use? How do we authenticate? Here you go.
There are two API’s available to work with Viva Engage (Yammer) from code:
- (modern) Microsoft Graph API
- (classic) Yammer API
Microsoft Graph API
Microsoft Graph API is a preferred way to work with Viva Engage programmatically. You’d just need an Entra Id App Registration configured correctly to authenticate and be authorized to call Graph API:
Unfortunately, Microsoft Graph API is still limited (Mar 2025) with respect to Viva Engage – you can only do CRUD operations against communities. You cannot search through community messages, you cannot post messages or read what is posted. You cannot reply or react on messages.
Since any Yammer community membership is based on Microsoft 365 group – you can use all group operations (including managing membership).
Since any Yammer community has a SharePoint site behind – you can use SharePoint Graph API to manage community documents.
Yammer API
Classic Yammer API is old, but still relevant API. With Classic Yammer API you can do what is not possible yet with Graph API, e.g. get messages (all or latest or within specific community or about some topic, etc.), search through messages, as well as post and delete messages.
Here is the full list of available operations. Unfortunately, Microsoft just keeps light on there (no plans for development). Below is how to authenticate to Yammer API and some usage samples of classic Yammer API for Viva Engage.
Update (May 2025): Private content mode will retire as of June 30th, 2025 (MC1045211)
This includes classic yammer API. Since Viva Engage (Yammer) communities access is now based on Microsoft 365 groups membership – you’d need to be a group member to access community messages via GUI or via classic Yammer API, (no exceptions after June 30th, 2025 MC1045211). Though export data will continue working as usual.
Register Yammer Application
Navigate to the page: https://www.yammer.com/client_applications
Click “Register new application”:
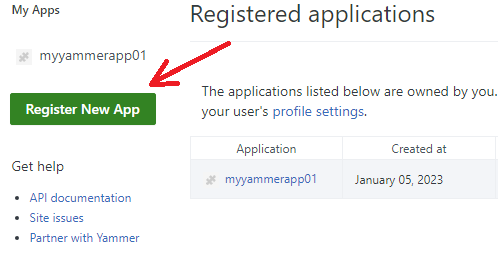
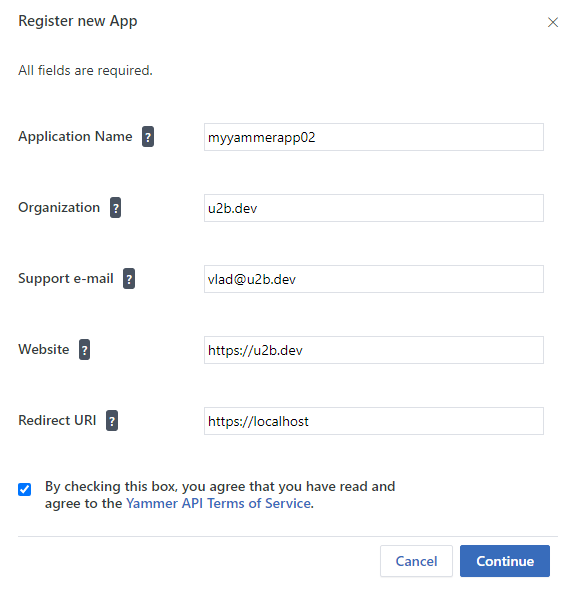
Fill all the fields:
Client ID and Client secret will be generated automatically:
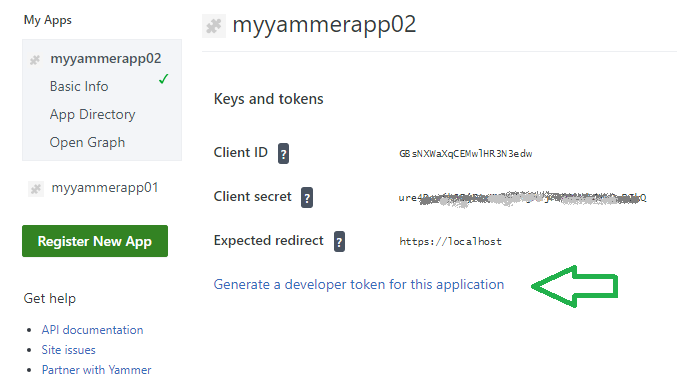
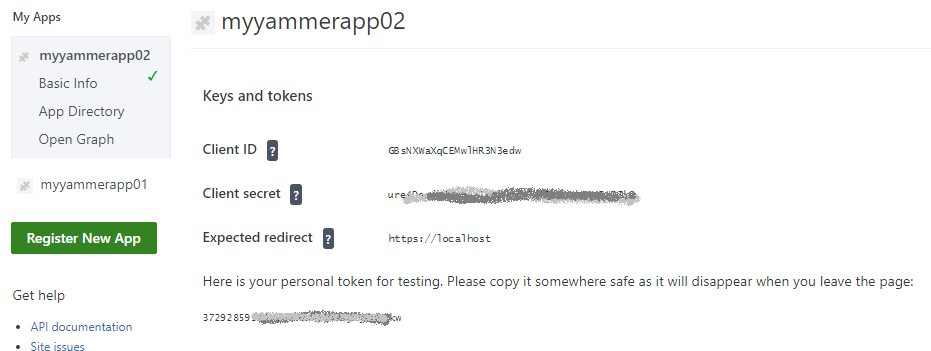
I’m not sure – how to get access token from Client ID and Client secret, so I use link “Generate a developer token for this application”. When you click this link, a token will be generated, and it says “Here is your personal token for testing. Please copy it somewhere safe as it will disappear when you leave the page:”
Calling Yammer API
Once you get the toke – you can use it in your code (consider vaulting or other save methods). Here is an example based on powershell, but surely you can do the same with programming language you comfortable with:
$baererToken = "Put your token here"
$headers = @{ Authorization = ("Bearer " + $baererToken) }
# get messages
$webRequest = Invoke-WebRequest –Uri "https://www.yammer.com/api/v1/messages.json" –Method Get -Headers $headers
$results = $webRequest.Content | ConvertFrom-Json
$results.messages | ForEach-Object {
$message = $_
Write-Host "Message Id:" $message.id
Write-Host "Message body:" $message.body.parsed
}
# get users
Invoke-WebRequest –Uri "https://www.yammer.com/api/v1/users.json" –Method Get -Headers $headers | ConvertFrom-Json | select email
# search through Viva Engage messages
$YammerApiURL = "https://www.yammer.com/api/v1/search.json?search=Test*"
$results = Invoke-WebRequest –Uri $YammerApiURL –Method Get -Headers $headers | ConvertFrom-Json
$results
$results.count
$results.users[0]
$results.messages.messages[0].body.parsed
# export all messages (admin role required)
$url = "https://www.yammer.com/api/v1/export?since=2020-02-9T00:00:00+00:00"
$url = $url + "&model=Message&include=csv"
Invoke-WebRequest –Uri $url –Method Get -Headers $headers | ConvertFrom-Json