





Search is everywhere in Microsoft 365. You can search from SharePoint, Teams, Delve, Yammer etc.
But! You cannot search for anything from everywhere!
Upd Oct 2025: Microsoft finished moving all services to cloud.microsoft and launched web-based Copilot and Search from m365.cloud.microsoft. E.g.
– Copilot: https://m365.cloud.microsoft/chat
– Search: https://m365.cloud.microsoft/search
What is interesting is search here works across all services – Exchange, SharePoint, Teams so from one place you can search content in emails, SharePoint pages, documents, lists, Teams chats.
Original article:
So, what are the scopes of each search entry point in Office 365 and is there an entry point you can search for everything?
| Search scopes | SharePoint Search center | SharePoint home Office portal Office desktop app Delve | Teams | Bing |
| SharePoint content | Yes | Yes | Yes | |
| Teams content | Yes | Yes | Yes | Yes |
| Teams chats | (*1) | Yes | Yes | |
| Yammer content | Yes | Yes | Yes | |
| Yammer chat | (*1) | Yes | ||
| User profiles | Yes | Yes | ||
Detailed:
| Scope | Out of Scope | |
| SharePoint Search Center | – all sites content (Teams, Yammer, regular), – user profiles – OneDrive | Teams chat Yammer chat |
| SharePoint Landing Page | same as SharePoint Search center but Teams chats and Yammer Conversations are coming | same as SharePoint Search Center |
| Office.com | same as SharePoint (Teams chats and Yammer Conversations are coming after SharePoint) | same as SharePoint |
| Delve | ||
| Teams | Teams content Teams chat | OneDrive Yammer User Profiles regular SharePoint sites |
| Bing | Everything* | * except people profiles content (e.g. about me) |
Seems like the only tool you can search for EVERYTHING with is Microsoft Bing:
Update: there are rumors that Microsoft is decommissioning work search in Bing… Pity… But something tells me that decomm is due to lack of usage/popularity, so Microsoft will introduce something similar…
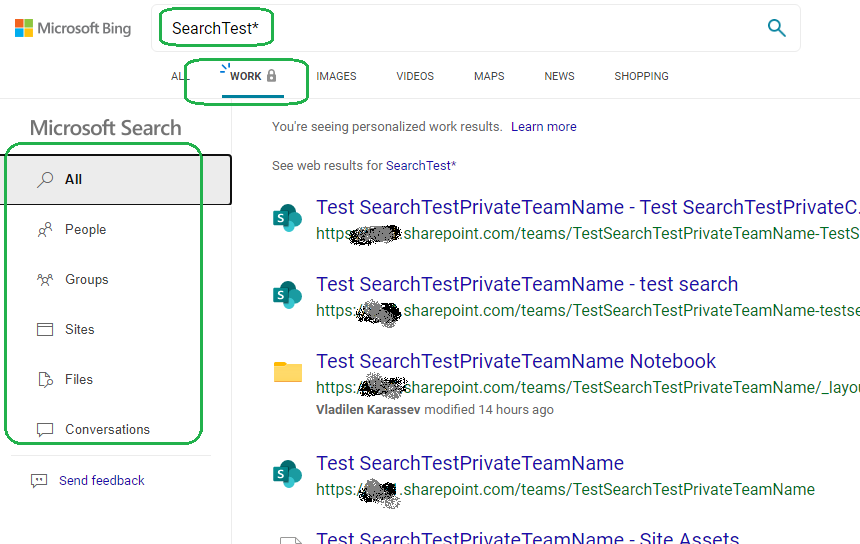
After Microsoft add Teams chats and Yammer conversations to SharePoint landing page search scope (then to Office home page) – it’ll be the best place to search from for everything.
More on Microsoft Search vs SharePoint Search and Microsoft Search RoadMap
Microsoft Office 365 Search: Find what you need with Microsoft Search in Bing
It is possible customize Modern Microsoft Search pages with PnP Modern Search
Почему бы не сделать виртуальные страны?Идея в том чтобы люди могли не сходя с места выбирать в какой стране жить.
Ситуация, когда общество расколото на две половины и каждая часть твёрдо стоит на своём и не желает идти на компромиссы напоминает мне что-то среднее между анекдотом когда два ковбоя бесплатно дерьма наелись и басней крылова “Лебедь, рак и щука”.
Я понимаю, если бы например одна партия имела перевес допустим в 80%, то она бы победила и вся страна, включая проигравшие 20% – забыли бы на 4-8 лет все обиды и вместе стали идти к светлому будущему, сообща и согласнованно строить новое лучшее общество.
Но ведь ситуация такая, что большого перевеса ни у кого нет уже долгое время. Страна разделена на две равные части и если одна выигрывает – то это не значит что другая соглашается с курсом – наоборот, другая остаётся при своих идеях, саботирует всё что только можно.
Получается чуть ли “Мы старый мир разрушим до основания а затем, мы наш мы новый мир построим. Кто был никем тот станет всем” каждые 4-8 лет.
Так почему бы каждой из этих половин не жить по тем законам, которые им нравятся? В нашем современном мире это должно быть технически осуществимо. Каждый человек раз в 4 года выбирает, по каким законам он хочет жить.
Если хочет, например, высокие налоги на бизнес, низкие налоги на зарплату, бесплатное образование, хорошую социальную защиту, ограничение на владение оружием и больше гражданский свобод – пусть живёт по законам виртуальной страны №1.
Если человек хочет запретить аборты и ЛГБТ браки, облегчить доступ к оружию, дорогую медицину и образование – пусть живёт в виртуальной стране номер два.
Тогда каждая виртуальная страна не будет тратить деньги на “разрушить старый мир и строить новый” каждые 4 года, а будет твёрдо идти в будущее своим курсом. Это же сколько денег можно сэкономить!
А конечная цель то у стран – одна – чтобы люди жили лучше. Средства достижения – разные. Вот и посмотрим, какая страна быстрее пойдёт к светлому будущему.
На возражение – “но ведь конкуренция между партиями – важная часть демократии и мы все видим к чему приводит партийные монополизм” – отвечу что а) Конкуренция не исчезает, а наоборот становится более честной, так как люди будут выбирать лидера не по голословным популистским заявлениям а по делам. Т.е. люди будут голосовать кошельком а не бумажками. иб) Монополизм (единоначалие, автократия) не всегда плохо. Плохо, когда это превращается в застой и отсутствие обратной связи на долгое время. Плохо, когда население не может “голосовать ногами”. В проектном менеджменте по-моему есть такое что демократия нужна на этапе выбора пути, а вот на этапе исполнения нужна “твёрдая рука”.
Я понимаю, что есть такие хитрецы, которые пока хорошо зарабатывают и не болеют – будут жить в одной стране, а в случае чего захотят переметнуться. Это можно сделать через “доплати”. В технологически развитой стране, где все транзакции электронные – это можно делать автоматически.
Трудности, конечно могут возникнуть например с внешней политикой или с армией. Полицейский же не должен думать – в какой виртуальной стране живёт человек прежде чем его защищать. Но вообще я думаю что все технические моменты можно решить, было бы желание.
Можно даже не две виртуальные страны сделать – а больше. Можно даже сделать мини-виртуальные страны и двойное – тройное виртуальное гражданство. Например, по отношению к внешней политике я выбираю страну В1, по здавоохранению я живу в стране Б5, и чту гражданский кодекс страны Г7.
И не обязательно в рамках одной физической…?
Корпоративные лицензии – это самый удобный для организаций способ лицензирования продуктов Microsoft.
КОРПОРАТИВНЫЕ ЛИЦЕНЗИИ
Это именные, непередаваемые, неисключительные лицензии, которые выпускаются компанией Microsoft индивидуально для каждого клиента.
Поставляются в виде запечатанного конверта, в котором находится документ с указанием наименования компании-обладателя лицензии, списка лицензированных продуктов и других реквизитов. Срок поставки электронных ключей составляет 2-5 дней, лицензий в бумажном виде – 7-10 дней.
VLSC (VOLUME LICENSING SERVICE CENTER)
С практической точки зрения большую ценность представляет доступ к сайту VLSC – Volume Licensing Service Center. При покупке корпоративных лицензий Microsoft клиент получает доступ через этот сайт к дистрибутивам продуктов и их ключам. Доступ к сайту открывается обычно в течение 2-3 дней после покупки. Доступ к сайту VLSC сначала предоставляется сотруднику, который отвечает за лицензирование (например, системный администратор или юрист), позже он может предоставить доступ и другим сотрудникам организации.
По Корпоративным лицензиям можно купить только актуальную на текущий момент версию продукта (например, Windows 10, Windows Server 2019, SharePoint 2019), но корпоративная лицензия обычно включает право Downgrade, т.е. возможность пользоваться предыдущими версиями продукта.
Дистрибутивы и ключи к предыдущим версиям также доступны на VLSC.
Виды корпоративного лицензирования
Open License (OLP) – простой выкуп лицензий на конкретные продукты в собственность:
– Можно купить столько лицензий, сколько надо, но обычно не менее 5 шт. в первом закупе (в дальнейшем от 1 шт.)
Open Value (OV) – выкуп лицензий в собственность с оплатой в рассрочку на 3 года, равномерными платежами:
– Цена включает SA, но в дальнейшем SA покупать не обязательно ( т.е. в первые 3 года SA оплачено, далее – опция )
– Начальные затраты ниже, чем у OLP
– Есть скидки «за стандартизацию», т.е. при покупке лицензий на весь парк ПК – цены ниже
Open Value Subscription (OVS) – аренда лицензий с ежегодной оплатой (подписка на лицензии):
– Минимальные начальные затраты
– Право пользоваться всегда самыми последними версиями ПО ( т.е. SA всегда входит в цену )
– Можно увеличивать количество лицензий, уменьшать или отказываться от лицензий в зависимости от потребностей
– Оплата происходит раз в год – надо просто посчитать количество используемых лицензий и оплатить их. При этом, например, вновь купленные в течение года компьютеры тоже будут считаться лицензированными. Есть продукты по которым
– Возможен выкуп лицензий в постоянное пользование по истечении 3-х лет аренды
– Требуется “стандартизация”, т.е. лицензирование всех ПК ( Windows или CAL или Office )
ЧТО ТАКОЕ SA
SA – Software Assurance. Купив к продукту SA, клиент получает возможность использовать все новые версии продукта, выпускаемые в течение действия подписки. А также для некоторый продуктов ряд дополнительных преимуществ, таких как право на использование второй копии на личном домашнем компьютере, право использования ПО в виртуальной среде, право переноса лицензий в частное или публичное облако и т.п.
SA продаётся как подписка, т.е. на ограниченный срок (2-3года), который можно постоянно продлевать.
Open Licensing programs хорошо подходят организациям от 5 до 250 сотрудников.
Менее 5 сотрудников – проще купить “коробки” – box/retail версии продуктов.
Более 250 сотрудников – организация имеет право на EA – Enterprise Agreement.
Подробнее об Open Programs на сайте Microsoft:
– What are the Microsoft Open Programs?
Какую помощь оказывают партнёры Microsoft по лицензированию:
– Support Provided by Licensing Solution Partners
Как купить Microsoft
Option 1: прямо на сайте Microsoft :
– Office 365 for Home
– Office 365 for Business
– Azure subscription (начать бесплатно)
Option 2: через партнёров Microsoft :
– Find a Microsoft Solution provider
– Top 200 Partners
N739BN – 1978 CESSNA 172N aka “Skyhawk”






Hybridizer: Kordes
Year: 1964
Type: Hybrid Tea
Color: Lavender
Frafrance: Slight
Height: 24-28″
Disease: Susceptible
Zone: 7a-10b
Scott Hanselman at Ignite (session 9/23/2020) said: if you are at the beginning of your career, certification is important, but if you have experience – experience matters, not certs. In other words – certification shows what you learned, experience shows what you know.
Does certification prove what you know?
It does in some ways, but I would not rely heavily on it. The reason is below…
To get certification in IT you’d need to pass one or more exams. To pass exam you need to prepare for the exam. Just knowing the subject – even with experience – is not enough to pass exam. You need to prepare specifically for this exam (there are specific courses, materials, tools etc.). Why? It’s not a subject experts who prepare exams.
People who prepare exams – are specialists in building tests and exams. What they do to create test questions – in simplified way – they read documentation trying to find key points and convert affirmative sentence from manual to a question. Let say the documentation says “The most important aspect of securing data is encryption.” So they put it like
What is the most important aspect of securing data? Options:
– Backup
– Encryption
– Authentication and authorization
– Access Control
or like this:
What is encryption? Options:
– The process of converting information or data into a code
– A way to conceal information by altering it
– A form of data security in which information is converted to ciphertext
– The most important aspect of securing data
– One of the aspects of securing data
So, having 10 years experience in cyber security – do you think you’ll pass such exam?
So to pass exam you need to memorize the right answers. If you know the subject – it helps. Less to memorize. But if you do not – you can just memorize answers and pass exam.
I know, vendors work hard on exams, they do not want to loose reputation. Exams contain not only such questions but some really good questions, and even complex scenarios where you spend first 10 minutes just trying to wrap your head around all the details… but still…
Does certification help if you already know the subject?
Definitely yes. Knowing the subject from practice – allows you to do the job – in most cases in some specific ways. But preparing for the exam – allows you to understand the whole big picture. Combination of your experience “how it works in fact” with the theory knowledge “how it should be done” is what you need to be an expert in your area.
So, the bottom line
Id’ say just certification does prove your competency.
But it definitely adds value to experience.
Good news!
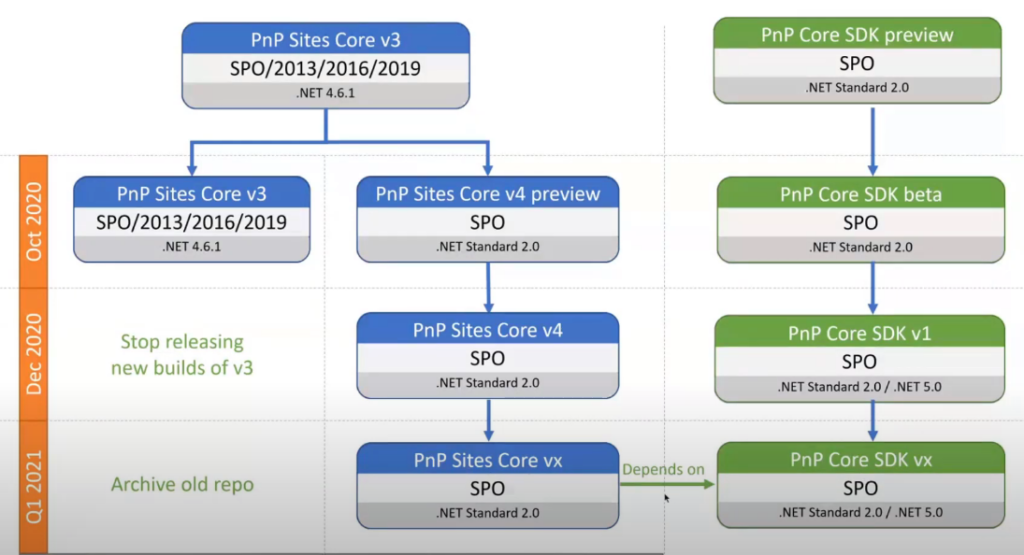
On Sep, 18 during the SIG community call, PnP Team shared their plans on PnP Sites Core library and PnP Core SDK.
“PnP Sites Core v4” library and “PnP Core SDK v1” with .net core support (.net Standard 2.0) – expected in December 2020!
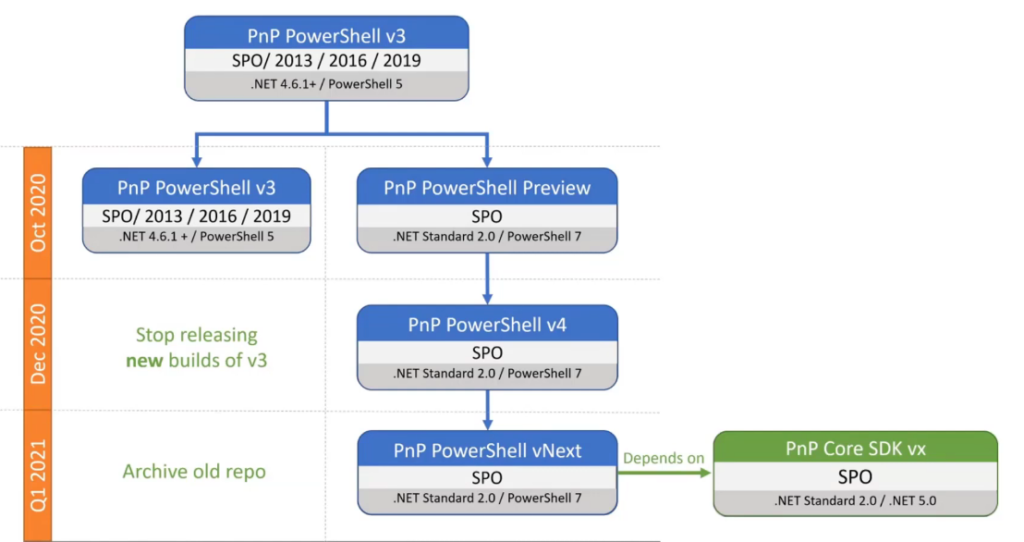
PnP PowerShell v4 for SPO library built for .Net Standard 2.0 / PowerShell 7 will be released in Dec 2020 as well.
Scenario: You have a large (>5k items) list in SharePoint Online you need to clean-up, for instance:
There was a problem in SharePoint Online – you could not delete a large list – you had to remove all items first, but removing all items was also a challenge. Microsoft improved SharePoint Online, so now it takes ~1 second to delete any SharePoint list, including 5000+ items list via GUI or PowerShell:
Remove-PnPList -Identity $listcommand works very fast – ~1 second to delete entire list with >5000 items.
In this scenario we need to keep the list, but make it empty (clean it up).
GUI: You can change the list view settings “Item Limit” to <5000 and try to delete items in chunks, but (at least in my experience) when you try to select, let say, 1000 items and delete them via GUI – it says “775 items were not deleted from large list”:
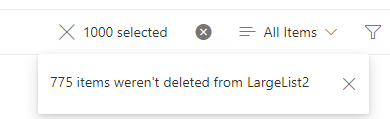
so this option seems like not a good one.
ShareGate: 3-rd party tools like Sharegate, SysKit give a good results too.
PowerShell
Try this PowerShell command with ScriptBlock:
Get-PnPListItem -List $list -Fields "ID" -PageSize 100 -ScriptBlock { Param($items) $items | Sort-Object -Property Id -Descending | ForEach-Object{ $_.DeleteObject() } }
or this PowerShell with batches:
$batch = New-PnPBatch
1..12000 | Foreach-Object { Remove-PnPListItem -List $list -Identity $_ -Batch $batch }
Invoke-PnPBatch -Batch $batchfor me both methods gave same good result: ~17 items per second ( ~7 times faster than regular).
Consider the following scenario: in a large SharePoint list there are items you need to delete and the rest items must stay (typical case might be to purge old items – e.g. items created last year).
In this case you’d
# to get all list items
$listItems = Get-PnPListItem -List Tasks -PageSize 1000
# or to get some list items
$listItems = Get-PnPListItem -List Tasks -Query <query>
# select items to delete
$itemsToDelete = $listItems | ?{$_.Modified -lt $threshold}
# delete some list items
$batch = New-PnPBatch
$itemsToDelete | Foreach-Object { Remove-PnPListItem -List $list -Identity $_ -Batch $batch }
Invoke-PnPBatch -Batch $batchHow fast are PnP batches? What is better in terms of performance – ScriptBlock or Batching? Here are my measurements:
| Time elapsed, seconds | with batches | with scriptBlock | without batches |
| Add-PnPListItem (100 items) | 6-10 seconds | 60-120 seconds | |
| Add-PnPListItem (500 items) | 20-40 seconds | 230-600 seconds | |
| Add-PnPListItem (7000 items) | 314-600 seconds | ||
| Add-PnPListItem (37000 items) | 3200 seconds | ||
| Remove-PnPListItem (1000 items) | 58-103 seconds | 58 seconds | 430-1060 seconds |
| Remove-PnPListItem (7000 items) | 395-990 seconds 3000 seconds | 397-980 seconds | |
| Remove-PnPListItem (30000 items) | one big batch : 13600 seconds 30 batches 1000 items each: 3500 seconds |
both – PnP PowerShell batches and ScriptBlocks are 7-10 times faster than plain PnP PowerShell!
Can we use Microsoft Graph API to complete the same task? TBC…
Note… For the sake of history: It used to be like that for 5k+ lists:
“Remove-PnPList” fails with a message “The attempted operation is prohibited because it exceeds the list view threshold enforced by the administrator”. Deleting with GUI failed too.
References: